攻防世界crypto:cr2-many-time-secrets
这题打开是这样的:
0529242a631234122d2b36697f13272c207f2021283a6b0c7908
2f28202a302029142c653f3c7f2a2636273e3f2d653e25217908
322921780c3a235b3c2c3f207f372e21733a3a2b37263b313012
2f6c363b2b312b1e64651b6537222e37377f2020242b6b2c2d5d
283f652c2b31661426292b653a292c372a2f20212a316b283c09
29232178373c270f682c216532263b2d3632353c2c3c2a293504
613c37373531285b3c2a72273a67212a277f373a243c20203d5d
243a202a633d205b3c2d3765342236653a2c7423202f3f652a18
2239373d6f740a1e3c651f207f2c212a247f3d2e65262430791c
263e203d63232f0f20653f207f332065262c3168313722367918
2f2f372133202f142665212637222220733e383f2426386b
刚开始以为是十六进制转化为ascii进行移位,无果。
了解了新知识点——Crib dragging attack
实现这种攻击的脚本:
GitHub - SpiderLabs/cribdrag: cribdrag - an interactive crib dragging tool for cryptanalysis on ciphertext generated with reused or predictable stream cipher keys
下载上面的脚本,把题目给的密文合并成一行,并执行:
python cribdrag.py 密文
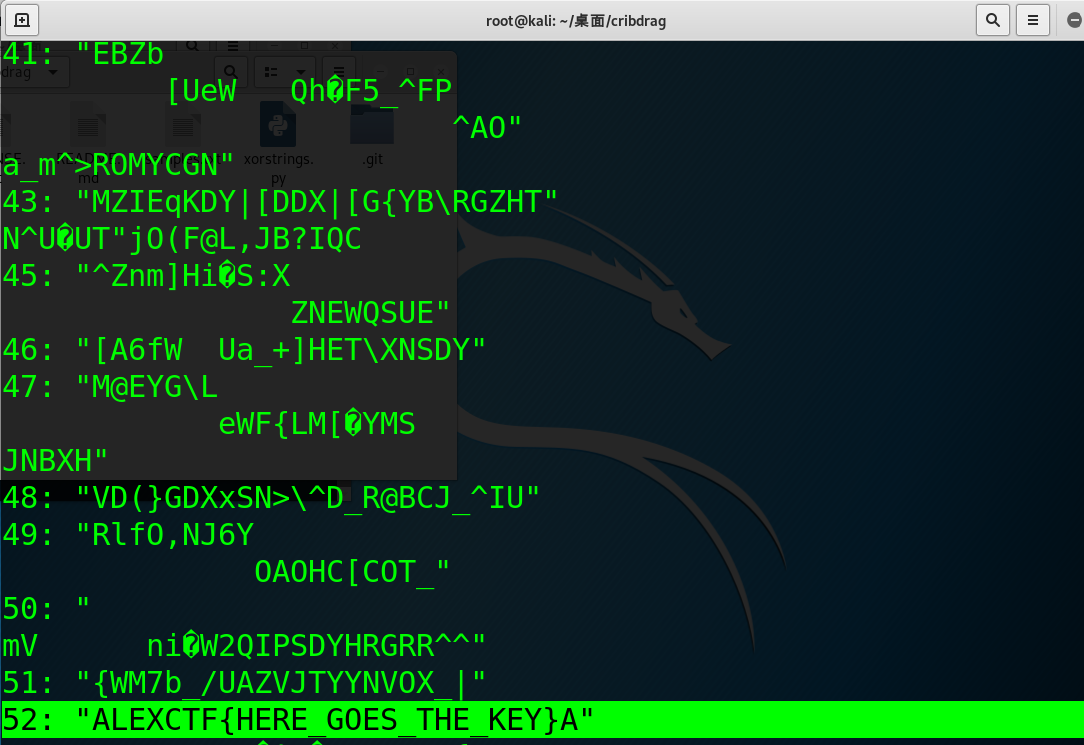
程序会提醒我们输入一个可能存在于明文或者密钥里的字符串,因为已知这个题目的flag格式是ALEXCTF{},所以输入“ALEXCTF{”,得到:
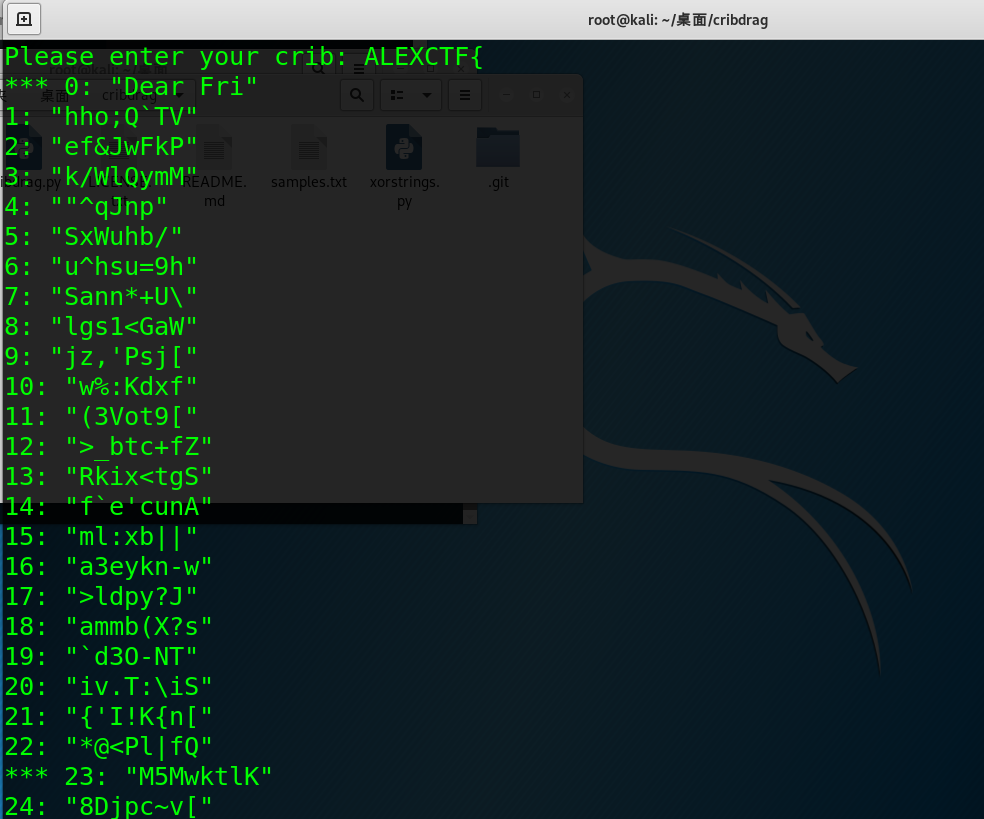
可以看到0这个选项就是有意义的字符串。程序又会提示我们输入我们的crib是明文中的还是密钥中的,假设flag是密钥,就输入key。
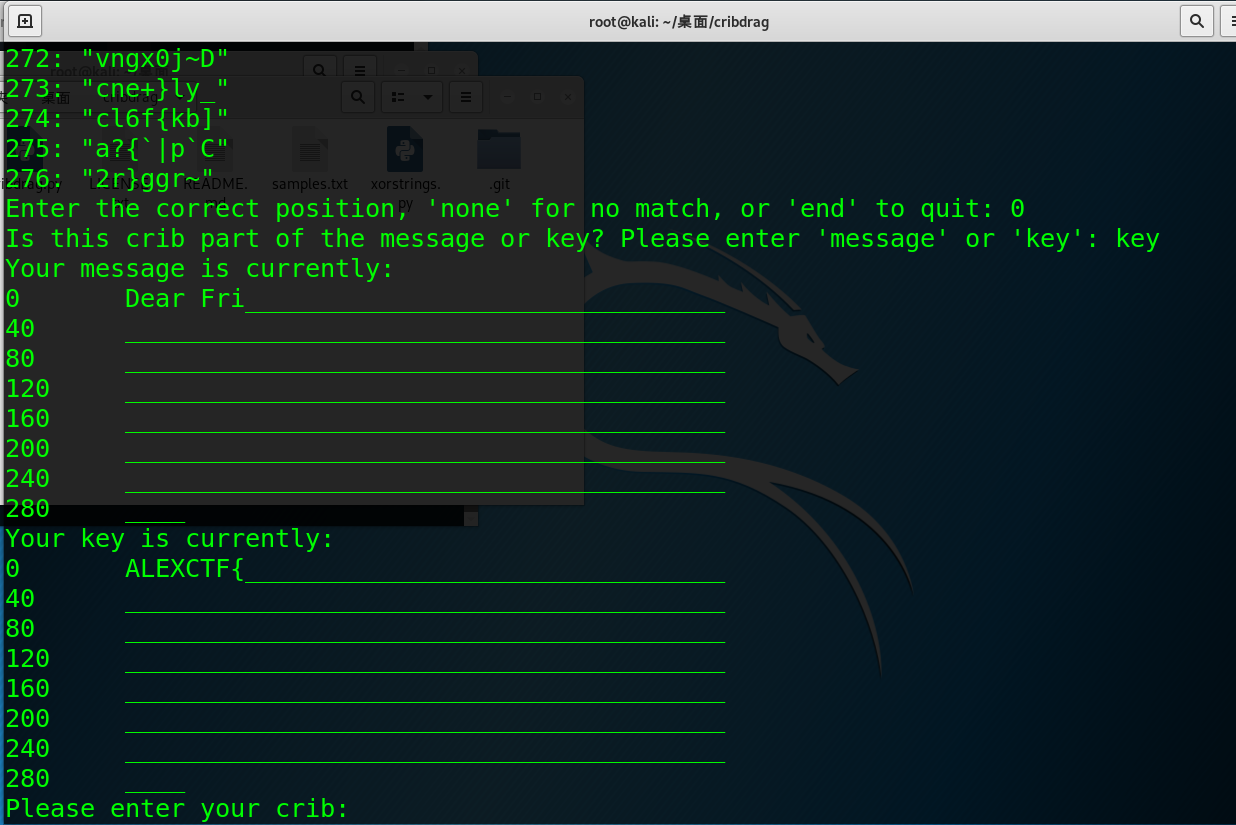
在刚才的结果中,不止0一个位置是有意义的,260号的 "ncryptio"也同样有意义。再次输入ALEXCTF{,输入260作为正确的位置。
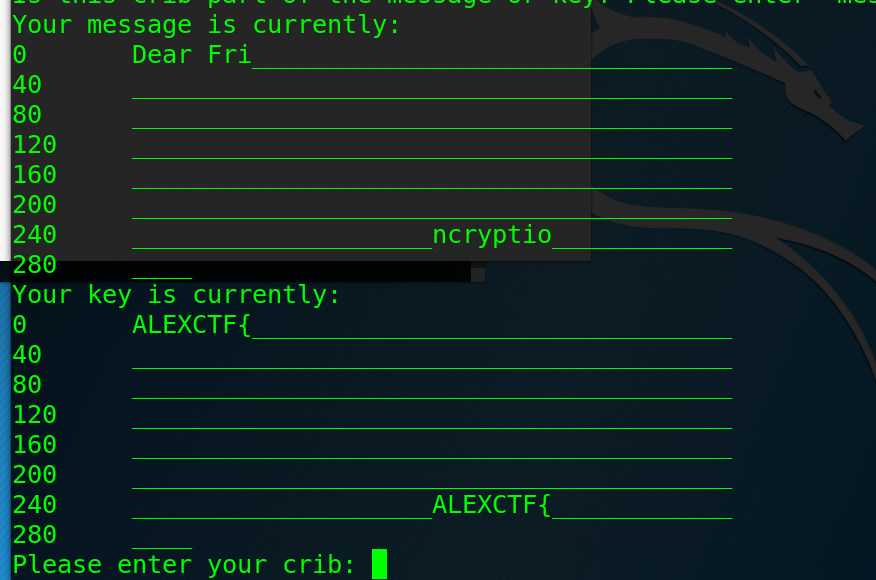
回到明文开头,我们可以猜测这是一封信的开头,Fri开头的单词很可能是Friend。输入“Dear Friend,”作为crib:
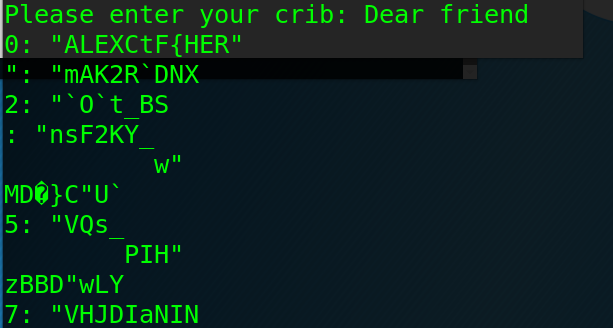
得到:0: "ALEXCTF{HER"
根据flag的常见格式,可以猜测HERE之后是下划线。将“ALEXCTF{HERE_”作为crib输入:
得到有意义的字符串有:
260: "ncryption sch"
234: "gree with me "
219: "a3iyip9Ff tao"
208: "cure, Let Me "
182: "ever if the k"
156: " proven to be"
139: "mm jeokMzpnic"
130: "hod that is m"
121: "nldrr?nGAlqd'"
113: "hg bjxqQgeson"
104: "is the only e"
78: "n scheme, I h"
52: "sed One time "
30: "qllLo1yG7otsx"
26: "nderstood my "
23: "M5MwktlKhlFi:"
0: "Dear Friend, "
找这里比较好猜的,之前已经才到有ncryptio,所以先看“ncryption sch”(260),很容易想到“ncryption scheme”,输入"ncryption scheme "作为crib:
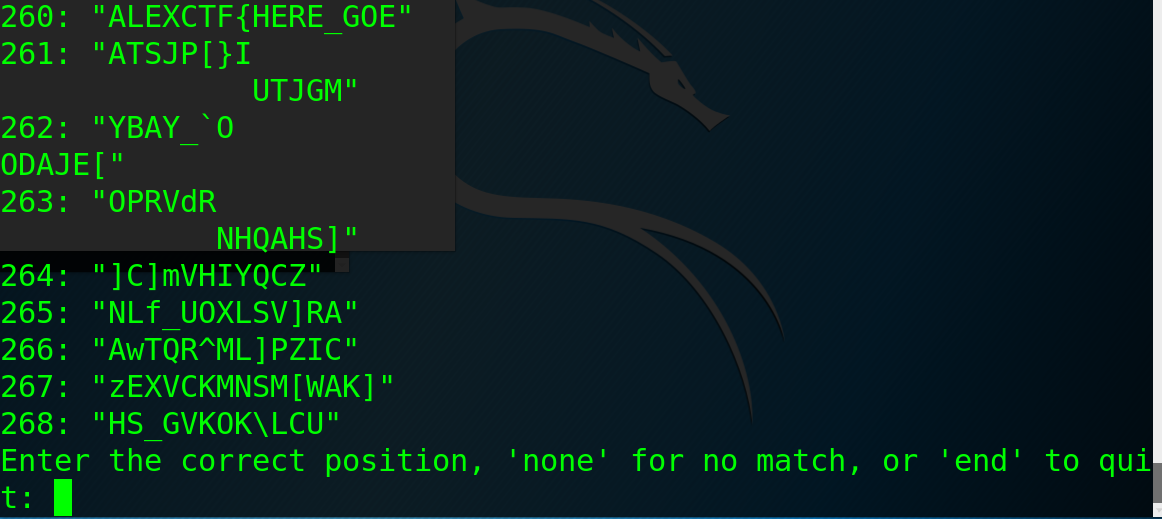
将ALEXCTF{HERE_GOE作为新的crib输入
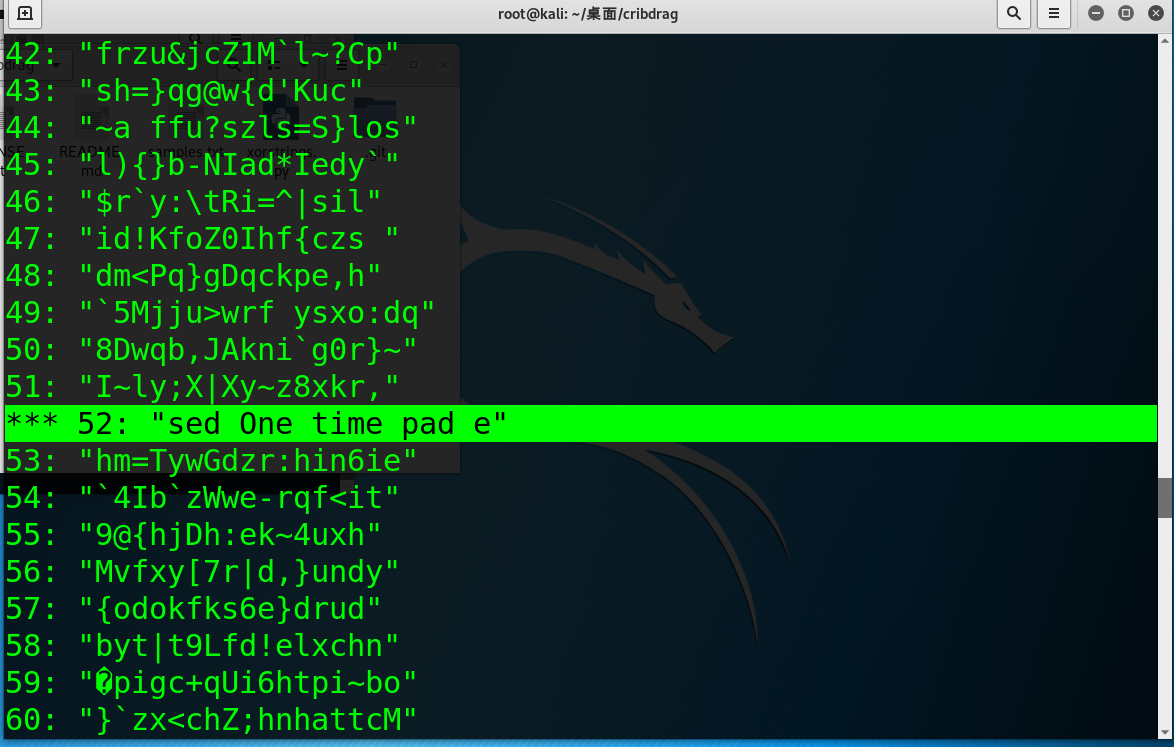
52的后面几乎可以确定是encryption,而且这样填充的字母多,所以这次输入"sed One time pad encryption":