UNCTF复现赛-Crypto部分做题记录
【 不仅仅是RSA 】
通过这个网站得到C1和C2的值
C1:4314251881242803343641258350847424240197348270934376293792054938860756265727535163218661012756264314717591117355736219880127534927494986120542485721347351 C2:485162209351525800948941613977942416744737316759516157292410960531475083863663017229882430859161458909478412418639172249660818299099618143918080867132349
利用openssl对两个公钥进行解密,得到n1n2和e1e2:
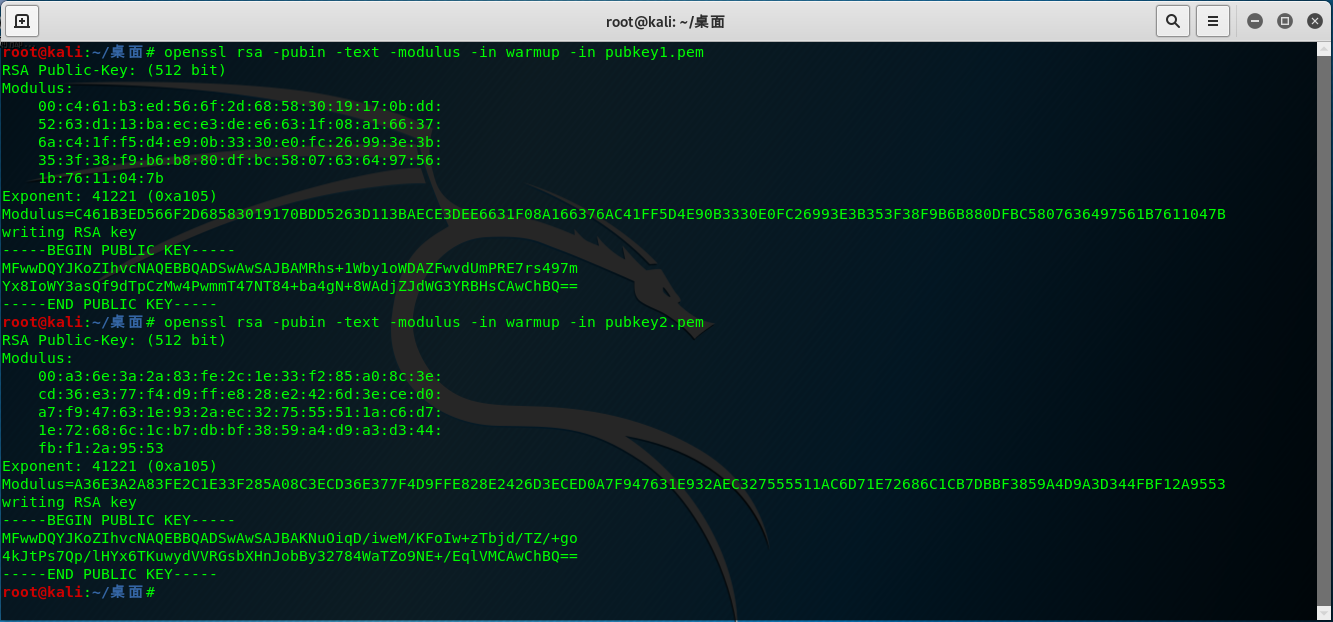
import gmpy2 import libnum n1 = gmpy2.mpz(10285341668836655607404515118077620322010982612318568968318582049362470680277495816958090140659605052252686941748392508264340665515203620965012407552377979) n2 = gmpy2.mpz(8559553750267902714590519131072264773684562647813990967245740601834411107597211544789303614222336972768348959206728010238189976768204432286391096419456339) e1 = 41221 e2 = 41221 p = gmpy2.gcd(n1,n2) q1 = n1 / p q2 = n2 / p c1 = 4314251881242803343641258350847424240197348270934376293792054938860756265727535163218661012756264314717591117355736219880127534927494986120542485721347351 c2 = 485162209351525800948941613977942416744737316759516157292410960531475083863663017229882430859161458909478412418639172249660818299099618143918080867132349 phin1 = (p - 1)*(q1 - 1) phin2 = (p - 1)*(q2 - 1) d1 = gmpy2.invert(e1,phin1) d2 = gmpy2.invert(e2,phin2) print(libnum.n2s(pow(c1,d1,n1))+libnum.n2s(pow(c2,d2,n2)))
运行得到flag:UNCTF{ac01dff95336aa470e3b55d3fe43e9f6}
【 一句话加密 】
下载下来有两个东西:
encode.py里仅仅有三行代码:
c = pow(int(m.encode('hex'), 16),e,n) c1:62501276588435548378091741866858001847904773180843384150570636252430662080263 c2:72510845991687063707663748783701000040760576923237697638580153046559809128516
得找到e和n
当时比赛的时候就没看懂这个e.png是个什么神仙东西QAQ...
把e.png用010editor打开,在结尾找到可疑的16进制字符串,应该是n,
和一个疑似hint的东西:
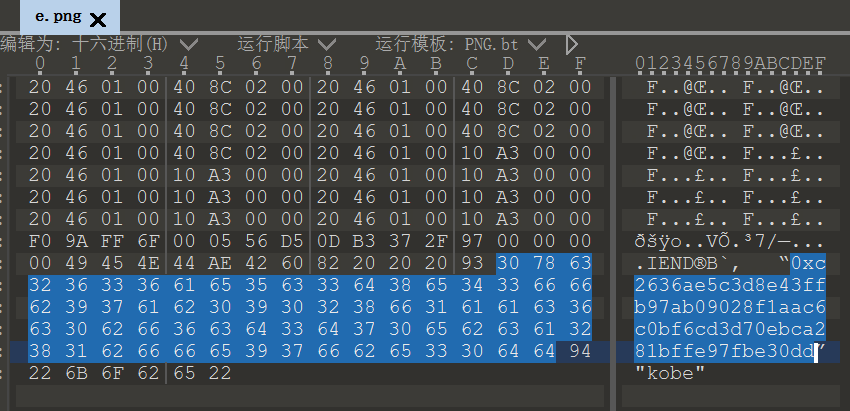
得知这个密码是kobe code:
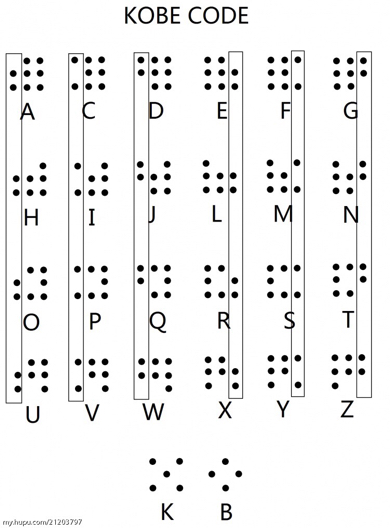
这样就得到了n和e,分解n得到p和q,而且e为2,这个叫Rabin加密,修改C,运行两次脚本得到flag。
import gmpy2,libnum n=0xc2636ae5c3d8e43ffb97ab09028f1aac6c0bf6cd3d70ebca281bffe97fbe30dd p=275127860351348928173285174381581152299 q=319576316814478949870590164193048041239 e=2 c=62501276588435548378091741866858001847904773180843384150570636252430662080263 mp=pow(c,(p+1)/4,p) mq=pow(c,(q+1)/4,q) yp=gmpy2.invert(p,q) yq=gmpy2.invert(q,p) r=(yp*p*mq+yq*q*mp)%n rr=n-r s=(yp*p*mq-yq*q*mp)%n ss=n-s print libnum.n2s(r) print libnum.n2s(rr) print libnum.n2s(s) print libnum.n2s(ss)
【 BABYRSA 】
我们亲爱的EDS师傅出的题(斜眼笑
开局的脚本里已经给出了n和e:
flag = open('flag.txt','r').read() N = 221 e = 5 enc = b'' for i in flag: enc += bytes([pow(ord(i),e,N)]) encrypt = open('encrypt','wb') encrypt.write(enc) encrypt.close()
求出p和q为13和17,万事俱备,只差密文啦。
a = open("encrypt",'rb') b = a.read() for i in b: print(i,end=",")
得到:
102,91,84,67,83,106,121,29,29,33,51,52,109,51,85,85,218,191,54,109,85,33,52,175,186,115,29,109,172,52,85,66,191,51,186,29,175,29,177
对密文逐个进行解密:
import gmpy2 import libnum p = 13 q = 17 e = 5 s = (p- 1) * (q - 1) d = long(gmpy2.invert(e, s)) n = p *q b = '' a = [102,91,84,67,83,106,121,29,29,33,51,52,109,51,85,85,218,191,54,109,85,33,52,175,186,115,29,109,172,52,85,66,191,51,186,29,175,29,177] for i in a: b += libnum.n2s(pow(i,d,n)) print b
运行得到flag:UNCTF{10023493ff87a9f246eb09d4f573e060}