BUUCTF/AFCTF2018-Crypto:可怜的RSA
拿到公钥:
-----BEGIN PUBLIC KEY----- MIIBJDANBgkqhkiG9w0BAQEFAAOCAREAMIIBDAKCAQMlsYv184kJfRcjeGa7Uc/4 3pIkU3SevEA7CZXJfA44bUbBYcrf93xphg2uR5HCFM+Eh6qqnybpIKl3g0kGA4rv tcMIJ9/PP8npdpVE+U4Hzf4IcgOaOmJiEWZ4smH7LWudMlOekqFTs2dWKbqzlC59 NeMPfu9avxxQ15fQzIjhvcz9GhLqb373XDcn298ueA80KK6Pek+3qJ8YSjZQMrFT +EJehFdQ6yt6vALcFc4CB1B6qVCGO7hICngCjdYpeZRNbGM/r6ED5Nsozof1oMbt Si8mZEJ/Vlx3gathkUVtlxx/+jlScjdM7AFV5fkRidt0LkwosDoPoRz/sDFz0qTM 5q5TAgMBAAE= -----END PUBLIC KEY-----
用openssl分解出n和e:
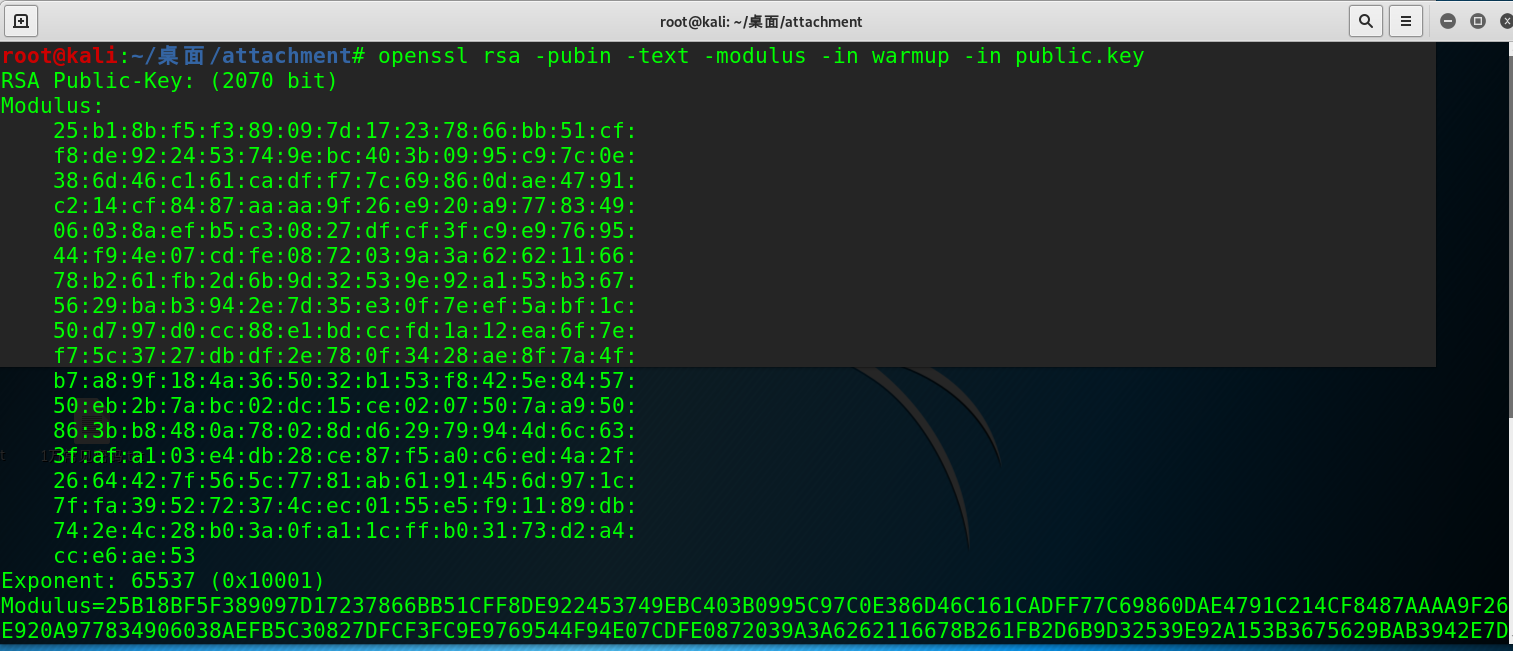
openssl rsa -pubin -text -modulus -in warmup -in public.key
n = 0x25B18BF5F389097D17237866BB51CFF8DE922453749EBC403B0995C97C0E386D46C161CADFF77C69860DAE4791C214CF8487AAAA9F26E920A977834906038AEFB5C30827DFCF3FC9E9769544F94E07CDFE0872039A3A6262116678B261FB2D6B9D32539E92A153B3675629BAB3942E7D35E30F7EEF5ABF1C50D797D0CC88E1BDCCFD1A12EA6F7EF75C3727DBDF2E780F3428AE8F7A4FB7A89F184A365032B153F8425E845750EB2B7ABC02DC15CE0207507AA950863BB8480A78028DD62979944D6C633FAFA103E4DB28CE87F5A0C6ED4A2F2664427F565C7781AB6191456D971C7FFA395272374CEC0155E5F91189DB742E4C28B03A0FA11CFFB03173D2A4CCE6AE53 e = 0x10001
尝试对n进行分解:
网址:http://factordb.com p = 3133337 q = 25478326064937419292200172136399497719081842914528228316455906211693118321971399936004729134841162974144246271486439695786036588117424611881955950996219646807378822278285638261582099108339438949573034101215141156156408742843820048066830863814362379885720395082318462850002901605689761876319151147352730090957556940842144299887394678743607766937828094478336401159449035878306853716216548374273462386508307367713112073004011383418967894930554067582453248981022011922883374442736848045920676341361871231787163441467533076890081721882179369168787287724769642665399992556052144845878600126283968890273067575342061776244939
生成私钥(private.pem):
#coding=utf-8 import math import sys from Crypto.PublicKey import RSA arsa=RSA.generate(1024) arsa.p=3133337 arsa.q=25478326064937419292200172136399497719081842914528228316455906211693118321971399936004729134841162974144246271486439695786036588117424611881955950996219646807378822278285638261582099108339438949573034101215141156156408742843820048066830863814362379885720395082318462850002901605689761876319151147352730090957556940842144299887394678743607766937828094478336401159449035878306853716216548374273462386508307367713112073004011383418967894930554067582453248981022011922883374442736848045920676341361871231787163441467533076890081721882179369168787287724769642665399992556052144845878600126283968890273067575342061776244939 arsa.e=65537 arsa.n=arsa.p*arsa.q Fn=long((arsa.p-1)*(arsa.q-1)) i=1 while(True): x=(Fn*i)+1 if(x%arsa.e==0): arsa.d=x/arsa.e break i=i+1 private=open('private.pem','w') private.write(arsa.exportKey()) private.close()
最后flag.enc还需要解base64(这里还有点疑问,先记录一下):
def decrypt_RSA(privkey, message): from Crypto.PublicKey import RSA from Crypto.Cipher import PKCS1_OAEP from base64 import b64decode key = open(privkey, "r").read() rsakey = RSA.importKey(key) rsakey = PKCS1_OAEP.new(rsakey) decrypted = rsakey.decrypt(b64decode(message)) return decrypted flag = "GVd1d3viIXFfcHapEYuo5fAvIiUS83adrtMW/MgPwxVBSl46joFCQ1plcnlDGfL19K/3PvChV6n5QGohzfVyz2Z5GdTlaknxvHDUGf5HCukokyPwK/1EYU7NzrhGE7J5jPdi0Aj7xi/Odxy0hGMgpaBLd/nL3N8O6i9pc4Gg3O8soOlciBG/6/xdfN3SzSStMYIN8nfZZMSq3xDDvz4YB7TcTBh4ik4wYhuC77gmT+HWOv5gLTNQ3EkZs5N3EAopy11zHNYU80yv1jtFGcluNPyXYttU5qU33jcp0Wuznac+t+AZHeSQy5vk8DyWorSGMiS+J4KNqSVlDs12EqXEqqJ0uA==" print decrypt_RSA('private.pem', flag)